
The digital environment for enterprises is becoming increasingly complex.
Not only hardware such as laptops and servers, but also SaaS, cloud applications, and countless commercial software tools are now essential to daily operations.
In this reality, the question “Are all of our company’s software assets being managed securely and efficiently?” has become a critical issue not just for IT teams but also for executives.
To address this challenge, many organizations deploy MDM (Mobile Device Management) or security solutions (DLP, EDR, etc.). These tools certainly play a vital role in areas such as device control and external threat detection. However, in practice, many companies conclude that “security solutions alone are not enough.”
Why? Because security-centric approaches are strong at blocking threats, but they fall short in meeting the essential needs of IT Asset Management (ITAM): operational optimization and cost control.
📌 Case 1 – Blocking worked, but no insight into why
A company adopted a DLP solution to prevent external security incidents. While it could block unauthorized software execution, there was no log of who ran it, when, or why.
As a result, repeated attempts by a particular department went unnoticed, and internal policy violations continued for months.
In today’s environment where new AI tools emerge constantly, a rigid whitelist-only blocking strategy can also hurt productivity.
👉 Blocking was possible, but without visibility into usage behavior, the root cause could not be addressed.
📌 Case 2 – Stronger security, but ongoing budget leaks
Another company deployed EDR to enhance security. However, it provided no visibility into how often high-cost tools like Adobe or AutoCAD were actually being used.
In reality, more than half of licensed users barely touched the tools.
👉 Millions of KRW in annual subscription fees were wasted, and the security solution could not reveal it.
📌 Case 3 – License compliance risks still present
One financial company enforced strict policies that blocked all newly installed software. Still, a team bypassed rules to install commercial tools for external collaboration—creating license compliance violations.
The security solution simply blocked execution but could not distinguish whether the software required a license or compliance management.
👉 Ultimately, this was exposed during an audit, creating serious legal risks.
In short, security solutions can block threats, but they have inherent limitations in providing integrated management across operations, costs, and compliance.
As an IT Asset Management solution, SELLEASE goes beyond simple blocking to provide a holistic system that combines security with operational oversight.
👉 Not only blocking, but also capturing behavioral data that enables fundamental improvements.
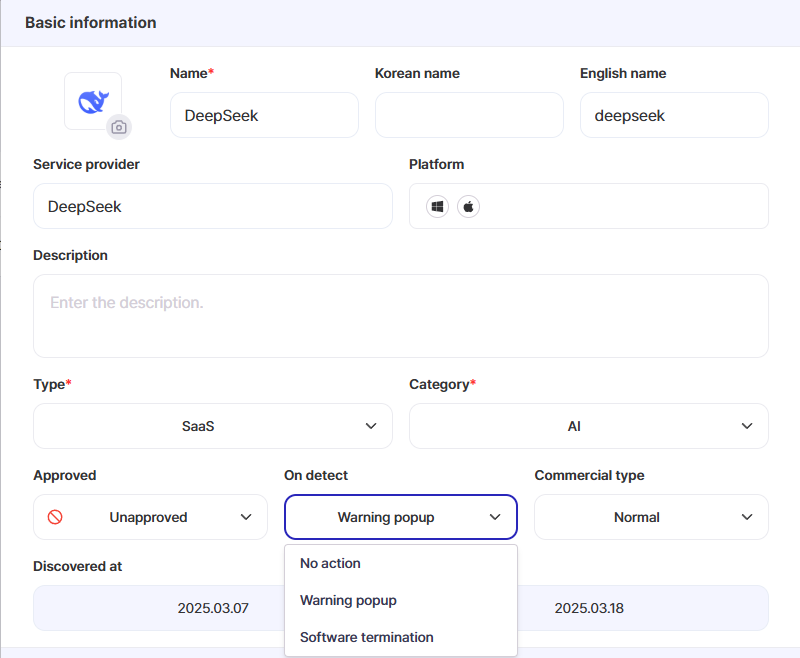
👉 This means not just stronger security, but also the ability to manage ROI (Return on Investment).
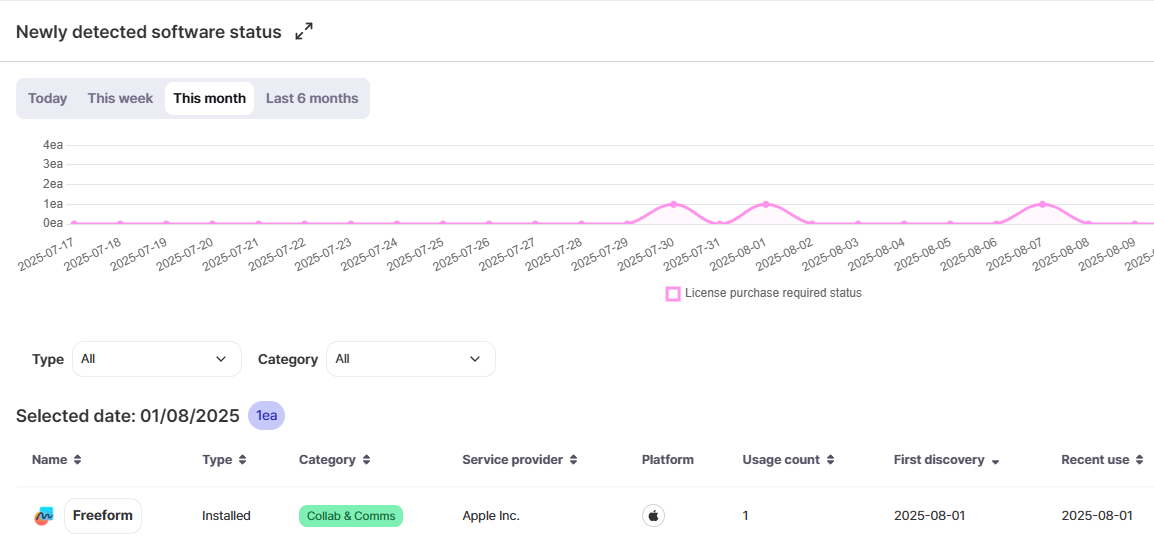
👉 Enables proactive legal compliance and provides audit-ready evidence.
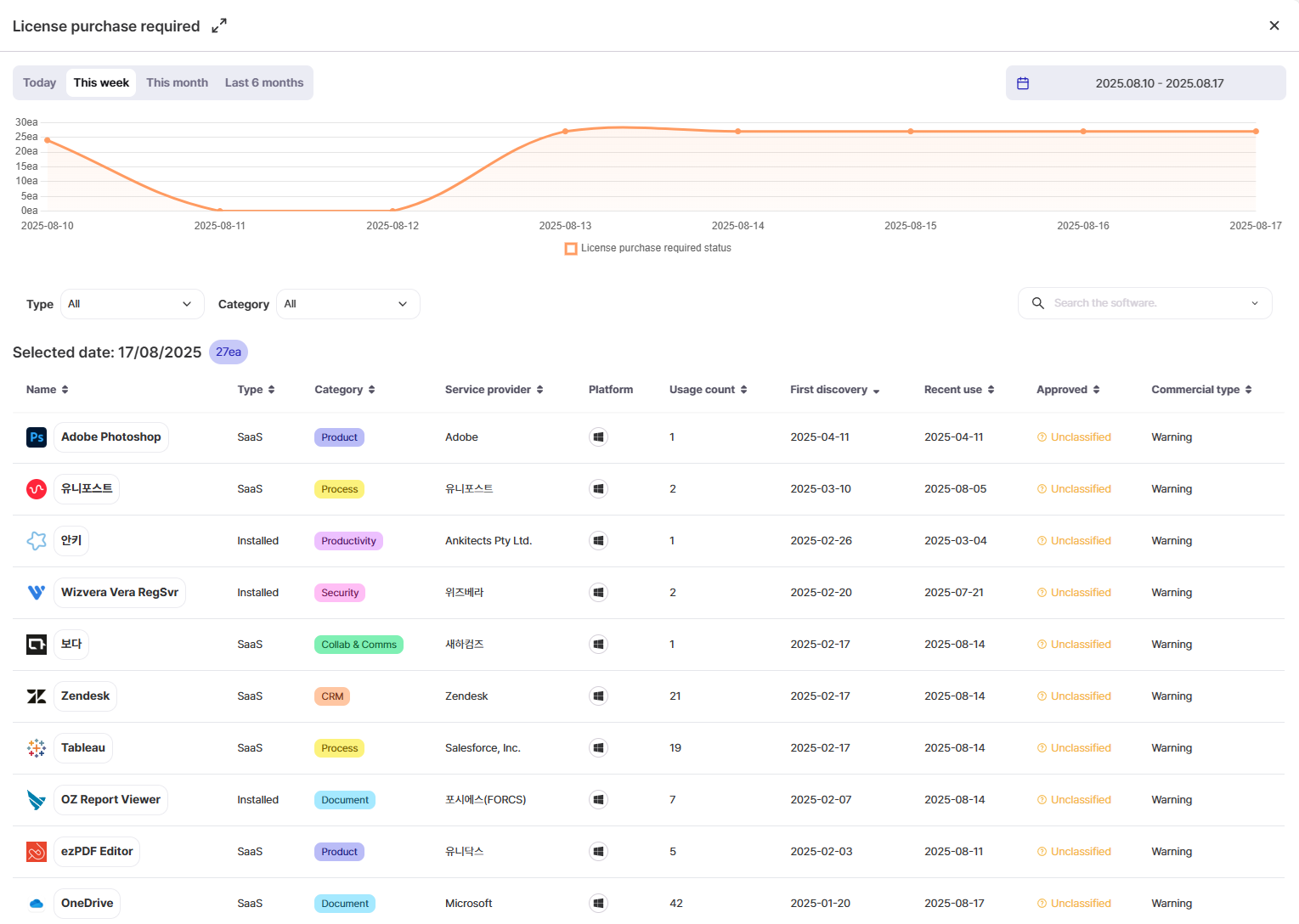
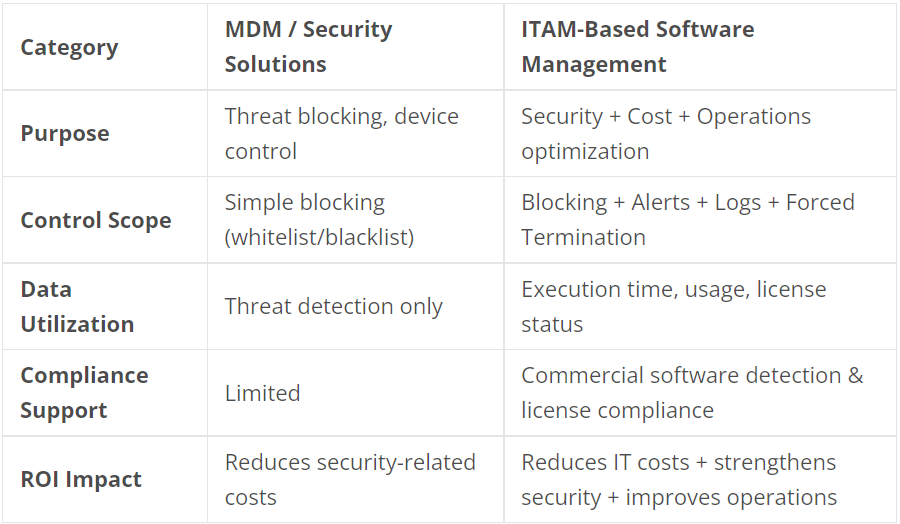
In other words, security solutions serve as a “shield,”
while ITAM-based software management functions as both a “shield and command center.”
Today, security solutions alone are no longer enough.
Enterprises must also manage how assets are used, where waste is occurring, and where compliance risks are hidden.
With SELLEASE, organizations gain:
Together, these capabilities fill the gaps left by traditional security tools.
👉 Now is the time for companies to manage software not only from a security perspective, but also through the lens of IT Asset Management.
That is the path to simultaneously achieving cost savings, stronger security, and operational efficiency.
